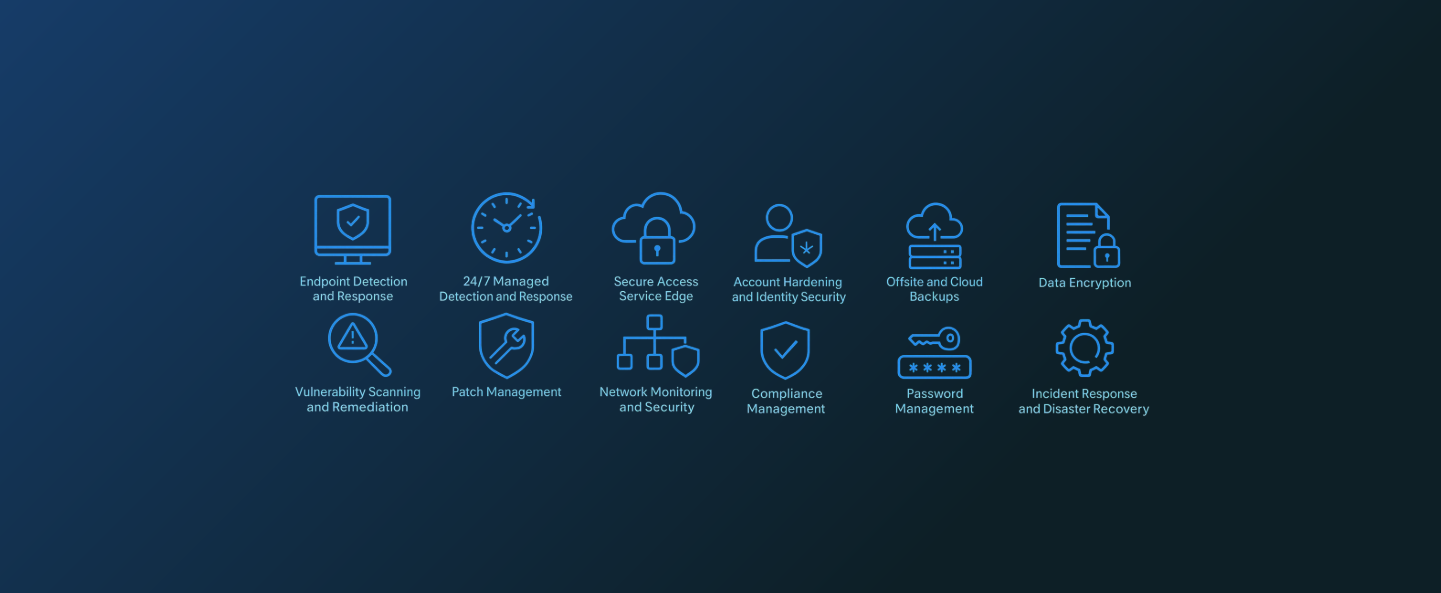
The Modern Threat Landscape Demands
More Than Single-Layer Protection
Cybersecurity is no longer a single product or control. It is an interconnected system of protections designed to reduce risk across endpoints, identities, networks, data, and users. As attack techniques evolve and environments become more distributed, organizations need layered defenses that work together rather than isolated tools operating independently.
This article outlines a modern cybersecurity stack and explains how each component contributes to real-world risk reduction.
Endpoint Detection and Response
Endpoints remain one of the most common entry points for cyber attacks. Laptops, desktops, and servers are constantly targeted through phishing, malicious downloads, and credential abuse.
Endpoint Detection and Response focuses on monitoring behavior at the device level rather than relying solely on signature-based detection. This allows suspicious activity such as ransomware execution, unauthorized privilege escalation, or abnormal system behavior to be identified early. When a threat is detected, affected devices can be isolated and remediated before the issue spreads across the environment.
This approach ensures endpoint protection remains effective even as attack methods change.
24/7 Managed Detection and Response (MDR),
Extended Detection and Response (EDR)
Detection without response creates blind spots. Modern environments generate more alerts than internal teams can realistically triage.
Managed Detection and Response provides continuous monitoring and active response to confirmed threats at the endpoint and network level. Extended Detection and Response expands this visibility across identity platforms, email systems, cloud services, and network infrastructure to identify coordinated or multi-stage attacks.
Alerts are investigated and acted on, not simply forwarded, ensuring real incidents receive timely response.
Secure Access Service Edge
Traditional perimeter-based security models assume users and systems operate inside a fixed network. That assumption no longer holds.
Secure Access Service Edge combines networking and security controls into a cloud delivered architecture that enforces access policies regardless of user location. Access to applications and data is secured consistently whether users are working remotely, in the office, or accessing cloud platforms.
This model is better suited for distributed organizations and reduces reliance on outdated perimeter defenses.
Vulnerability Scanning and Remediation
Unpatched systems and misconfigurations remain one of the most exploited attack vectors.
Continuous vulnerability scanning identifies weaknesses across systems, applications, and infrastructure. Findings are prioritized based on real-world exploitability rather than raw severity scores. Remediation efforts focus on closing the gaps that attackers are most likely to exploit.
This reduces exposure to known threats and supports regulatory and insurance requirements.
Patch Management
Many successful attacks rely on vulnerabilities that already have available fixes.
Patch management ensures operating systems, applications, and infrastructure components remain current with security updates. Updates are tested before deployment to minimize disruption while closing common attack paths used by ransomware and automated exploits.
Consistent patching significantly lowers overall risk and improves system stability.
Network Monitoring and Security
Networks serve as the connective tissue of modern organizations.
Without proper monitoring, malicious activity can go undetected for extended periods.
Network monitoring includes intrusion detection, traffic analysis, and alerting of infrastructural degradation. Continuous visibility helps identify anomalies, outages, and unauthorized access attempts before they escalate.
A well-monitored network supports both security and operational reliability.
Account Hardening and Identity Security
Compromised credentials, coupled with MFA token theft, is one of the most common causes of breaches.
Account hardening focuses on enforcing strong authentication policies, least-privilege access, and role-based controls. This includes multi-factor authentication, monitoring for suspicious login behavior, prevention of insecure or suspicious sign-in attempts, and reducing unnecessary access rights.
Strengthening identity security significantly reduces the risk of account takeover and internal misuse.
Offsite and Cloud Backups
Data loss can occur through ransomware, accidental deletion, or system failure.
Offsite and cloud backups ensure critical data can be restored quickly regardless of where it resides, including on-prem systems, Microsoft 365, and Google Workspace environments. Backups are encrypted, monitored, and regularly tested to confirm recovery readiness.
Reliable backups are a core component of business continuity planning.
Data Encryption
Encryption protects sensitive data even when other controls fail.
Encrypting data at rest and in transit ensures that intercepted or stolen data remains unreadable without proper authorization. This limits exposure during incidents and supports regulatory requirements.
Proper encryption safeguards data throughout its lifecycle.
Compliance Management
Security programs increasingly need to align with regulatory and insurance expectations.
Compliance management maps security controls to frameworks such as NIST, CIS, HIPAA, PCI, and cyber insurance standards. This includes enforcement policies, documentation, risk assessments, and ongoing maintenance to demonstrate security maturity.
Alignment reduces audit friction and improves organizational accountability.
Password Management
Weak or reused passwords continue to be a major source of compromise.
Password management tools centralize credential storage, enforce password policies, and integrate with multi-factor authentication. Secure credential sharing reduces risky workarounds and human error.
Strong credential hygiene helps prevent credential-based attacks.
Incident Response and Disaster Recovery
Preparation determines outcomes during a security incident.
Incident response and disaster recovery planning defines response procedures, escalation paths, and recovery objectives before incidents occur. When an event happens, systems can be contained and restored more efficiently.
Preparedness reduces downtime, financial impact, and reputational damage.
An Integrated Security Approach
These controls are most effective when they operate as a unified system.
Cybersecurity defines the strategy. Operational management maintains and enforces controls. Monitoring and response provide continuous protection.
Together, this layered approach delivers resilient security without unnecessary complexity.
Ready to understand where your
security actually stands?
Vision Quest helps organizations evaluate, implement, and maintain cybersecurity systems that are built for how work actually happens today. If you want clarity on gaps, risk, and next steps without noise or pressure, we’re here to help.