Email spoofing is simply someone pretending an email is from someone it isn’t, with a goal of getting you to respond. So you got an Email from your CEO/Controller/Boss asking if you are “in” or asking to transfer “funds” for a new vendor. Maybe you got an email from your email service provider asking you to reset your password. Unfortunately these are all too common and rarely legit, especially if it has generic information in it, and came out of the blue. Unfortunately this is escalating, and entities that require their internal positions be publicly known are getting hit hard. For example, a nonprofit needs to list their CEO, or controller on their website to get grants. Or a small city government is required to list the city manager’s name and email on the website. This makes it very easy to spoof.
Email works a quite similar to the snail mail postal service. There are rules you must follow to get an letter from point A to point B. Including a send to address, and (though not required) a return address. The problem with spoofing in the computer world is that it is just as easy to change the return address as it is for someone to write anything they want in the top left corner of the envelope saying who it was from. I, being a computer tech cannot stop someone in a 3rd world country from saying an email was really sent from myself, the same as I can’t force someone in another State to not write my home address on a piece of mail because it is following the established rules of how email and postal service work. Anyone with internet can create an email account called “CEOVQIS@gmail.com” (or yahoo.com, or mail.com juno.com, etc. ) and sign up with my name, in fact there are scripts that make hundreds of these emails a day. They will then email everyone at my office and say the “reply” to address is my email address, then they will move on to the next company. With this they can claim to have my name, and claim to have my email address. However it will show it was really SENT ON BEHALF of the true sending email (the CEOVQIS@gmail in our example) They then will ask to start an email dialog for social engineering, or to get passwords reset, or to create new vendors, etc.
There are some technologies coming around that put protection in place, to verify the emails are sent from the correct server it’s claiming to, and to verify they are who they say there are. However, if they say their name is John Doe, or your name, there is no way to verify that, so spoofing reaches most recipients and navigates past more online protections. There are advanced spam filters that do a pretty good job to help with spam as well as spoofing, however they can require end user management, due to the end users know what is spam FOR THEM, verses what may just look like spam.
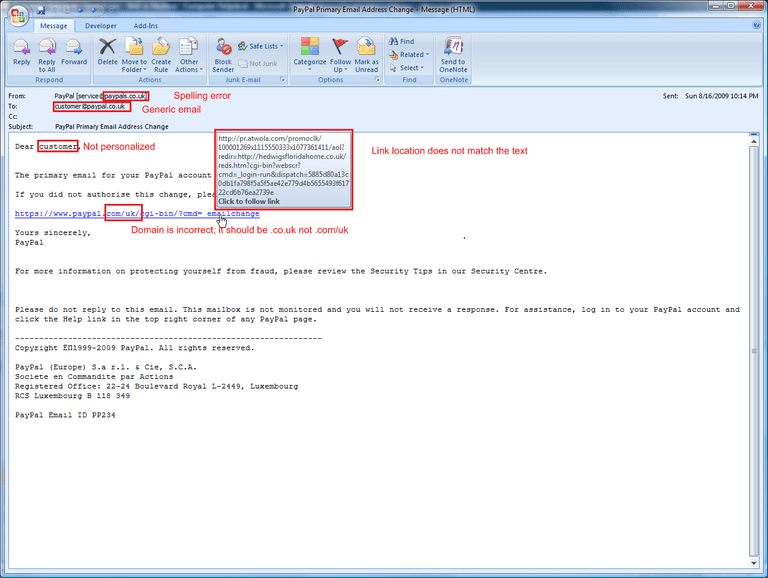
The best protection like with most forms of security is knowledge. In our example, if the email wasn’t expected, came out of the blue, and just has generic information in it, it deserves further review and scrutiny. From here look for spelling errors, (paypalS.com not paypal.com) double check the email address it was sent from, not just the name. Hover over any “links” and make sure they are legitimate links your company uses. To “reset your email password” The link isn’t going to be an odd ausadf.sau.haxed.TV domain for your email that is hosted at Microsoft.com.
In conclusion Knowledge is Power and protection, and there are ways to stop spoofing, though they might cause other problems as well. Spam unfortunately is still a battle we are fighting and the landscape is constantly changing. The best protection is a combination of training, anti virus software, spam filtering, and common sense. We can help with the first three.

